搜尋 validate 結果:
在 powershell 執行以下的指令
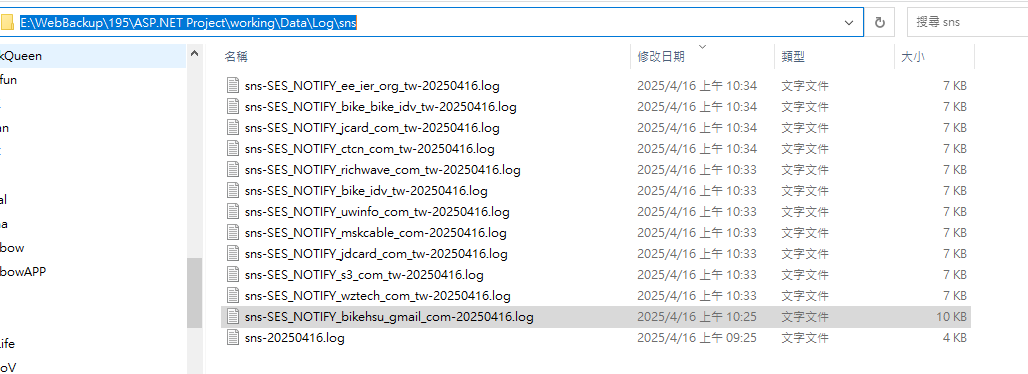
收到的 log 會放在這裡: E:\WebBackup\195\ASP.NET Project\working\Data\Log\sns
# List of SES identities
$identities = @(
"wztech.com.tw",
"s3.com.tw",
"jdcard.com.tw",
"mskcable.com",
"uwinfo.com.tw",
"bike.idv.tw",
"richwave.com.tw",
"ctcn.com.tw",
"jcard.com.tw",
"bike@bike.idv.tw",
"ee@ier.org.tw"
)
foreach ($identity in $identities) {
# Convert identity to a valid topic name by replacing '@' and '.' with '_'
$safeIdentity = $identity -replace "@", "_" -replace "\.", "_"
$topicName = "SES_NOTIFY_$safeIdentity"
$endpoint = "https://working.uwinfo.com.tw/aws/api/sns/receive?topic=$topicName"
# Validate topic name format
if ($topicName -notmatch '^[a-zA-Z0-9_\-\$]+$') {
Write-Host "❌ Invalid topic name: $topicName"
continue
}
# 1. Create SNS topic
$topicArn = aws sns create-topic `
--name $topicName `
--query 'TopicArn' `
--output text
Write-Host "✔ Created topic: $topicArn"
# 2. Subscribe webhook
aws sns subscribe `
--topic-arn $topicArn `
--protocol https `
--notification-endpoint $endpoint
Write-Host "✔ Subscribed webhook: $endpoint"
# 3. Link SES notifications
foreach ($type in @("Delivery", "Bounce", "Complaint")) {
aws ses set-identity-notification-topic `
--identity $identity `
--notification-type $type `
--sns-topic $topicArn
Write-Host "✔ $type linked to $topicName"
}
Write-Host "✅ Setup complete for $identity\n"
}
Write-Host "🎉 All identities processed."
收到的 log 會放在這裡: E:\WebBackup\195\ASP.NET Project\working\Data\Log\sns

Bike, 2025/4/16 上午 10:40:39
在 powershell 執行以下的指令
# List of SES identities
$identities = @(
"wztech.com.tw",
"s3.com.tw",
"jdcard.com.tw",
"mskcable.com",
"uwinfo.com.tw",
"bike.idv.tw",
"richwave.com.tw",
"ctcn.com.tw",
"jcard.com.tw",
"bike@bike.idv.tw",
"ee@ier.org.tw"
)
foreach ($identity in $identities) {
# Convert identity to a valid topic name by replacing '@' and '.' with '_'
$safeIdentity = $identity -replace "@", "_" -replace "\.", "_"
$topicName = "SES_NOTIFY_$safeIdentity"
$endpoint = "https://working.uwinfo.com.tw/aws/api/sns/receive?topic=$topicName"
# Validate topic name format
if ($topicName -notmatch '^[a-zA-Z0-9_\-\$]+$') {
Write-Host "❌ Invalid topic name: $topicName"
continue
}
# 1. Create SNS topic
$topicArn = aws sns create-topic `
--name $topicName `
--query 'TopicArn' `
--output text
Write-Host "✔ Created topic: $topicArn"
# 2. Subscribe webhook
aws sns subscribe `
--topic-arn $topicArn `
--protocol https `
--notification-endpoint $endpoint
Write-Host "✔ Subscribed webhook: $endpoint"
# 3. Link SES notifications
foreach ($type in @("Delivery", "Bounce", "Complaint")) {
aws ses set-identity-notification-topic `
--identity $identity `
--notification-type $type `
--sns-topic $topicArn
Write-Host "✔ $type linked to $topicName"
}
Write-Host "✅ Setup complete for $identity\n"
}
Write-Host "🎉 All identities processed."
--
收到的 log 會放在這裡: E:\WebBackup\195\ASP.NET Project\working\Data\Log\sns

# List of SES identities
$identities = @(
"wztech.com.tw",
"s3.com.tw",
"jdcard.com.tw",
"mskcable.com",
"uwinfo.com.tw",
"bike.idv.tw",
"richwave.com.tw",
"ctcn.com.tw",
"jcard.com.tw",
"bike@bike.idv.tw",
"ee@ier.org.tw"
)
foreach ($identity in $identities) {
# Convert identity to a valid topic name by replacing '@' and '.' with '_'
$safeIdentity = $identity -replace "@", "_" -replace "\.", "_"
$topicName = "SES_NOTIFY_$safeIdentity"
$endpoint = "https://working.uwinfo.com.tw/aws/api/sns/receive?topic=$topicName"
# Validate topic name format
if ($topicName -notmatch '^[a-zA-Z0-9_\-\$]+$') {
Write-Host "❌ Invalid topic name: $topicName"
continue
}
# 1. Create SNS topic
$topicArn = aws sns create-topic `
--name $topicName `
--query 'TopicArn' `
--output text
Write-Host "✔ Created topic: $topicArn"
# 2. Subscribe webhook
aws sns subscribe `
--topic-arn $topicArn `
--protocol https `
--notification-endpoint $endpoint
Write-Host "✔ Subscribed webhook: $endpoint"
# 3. Link SES notifications
foreach ($type in @("Delivery", "Bounce", "Complaint")) {
aws ses set-identity-notification-topic `
--identity $identity `
--notification-type $type `
--sns-topic $topicArn
Write-Host "✔ $type linked to $topicName"
}
Write-Host "✅ Setup complete for $identity\n"
}
Write-Host "🎉 All identities processed."
--
收到的 log 會放在這裡: E:\WebBackup\195\ASP.NET Project\working\Data\Log\sns

Bike, 2025/4/16 上午 10:40:31
以下的程式碼, 直接 alert(this.errorMessages); 會造成 chrome 卡住..
使用 setTimeout 延後 alert 可以解決這個問題. 但必需延後足夠的時間. 已知 200 ms 依然會卡住.
使用 setTimeout 延後 alert 可以解決這個問題. 但必需延後足夠的時間. 已知 200 ms 依然會卡住.
errorMessages: "",
failProcess: function (ret) {
console.log("failProcess start: " + new Date().getSeconds() + "." + new Date().getMilliseconds());
var json = ret.responseJSON;
if (json && json.invalidatedPayloads) {
var errors = json.invalidatedPayloads.filter(function F(x) {
return x.messages.length > 0
});
console.log("bdfore add class: " + new Date().getSeconds() + "." + new Date().getMilliseconds());
errors.map(function (x) {
return $("[name='" + x.name + "']").addClass("error");
});
console.log("after add class: " + new Date().getSeconds() + "." + new Date().getMilliseconds());
errorMessages = errors.map(function (x) {
return x.messages.join('\r\n');
}).join('\r\n');
console.log("afger build errorMessages: " + new Date().getSeconds() + "." + new Date().getMilliseconds());
console.log(errorMessages);
//alert(this.errorMessages);
window.setTimeout(api.alertError, 500);
console.log("after alert: " + new Date().getSeconds() + "." + new Date().getMilliseconds());
}
console.log("failProcess end: " + new Date().getSeconds() + "." + new Date().getMilliseconds());
},
Bike, 2021/9/29 下午 08:45:07
錯誤訊息如下, 完全沒有錯誤訊息, 以及沒有錯誤的程式碼位置
查了一下,原來網址後面多了空白 (%20) , 也就是 ? 前面多了空白
只是exception物件會自作聰明把他濾掉了,反而從 exception log 看不到資料
測試過,userd可以正常看網站,只是server會有不斷 excetion產生,有點煩
網路上雖有一些解法,但我想還是要求下廣告時,要注意網址問題
<Item time="2016-01-11T05:39:01" page="/fr/iconic-bright-cushion-spf-50-pa-nude-perfection-compact-foundation/p/5490/c/30"
url="http://www.shopunt.com/fr/iconic-bright-cushion-spf-50-pa-nude-perfection-compact-foundation/p/5490/c/30?utm_source=edm&utm_medium=email&utm_content=20160107_cushion_4&utm_campaign=makeup&OutAD_Id=5825" username="Not Member" browserName="Chrome" browserVersion="34.0" userAgent="Mozilla/5.0 (Linux; Android 5.1.1; SAMSUNG SM-N915FY Build/LMY47X) AppleWebKit/537.36 (KHTML, like Gecko) SamsungBrowser/2.1 Chrome/34.0.1847.76 Mobile Safari/537.36" RemoteIP="37.160.206.7" Ref="No Ref" RequestType="GET" Ver="3">
<ErrMsg>
</ErrMsg>
<ErrStack> 於 System.Web.CachedPathData.ValidatePath(String physicalPath)
於 System.Web.HttpApplication.PipelineStepManager.ValidateHelper(HttpContext context)</ErrStack>
<Post>
</Post>
<Cookie>
</Cookie>
</Item>
查了一下,原來網址後面多了空白 (%20) , 也就是 ? 前面多了空白
只是exception物件會自作聰明把他濾掉了,反而從 exception log 看不到資料
測試過,userd可以正常看網站,只是server會有不斷 excetion產生,有點煩
網路上雖有一些解法,但我想還是要求下廣告時,要注意網址問題
darren, 2016/1/11 上午 09:51:49
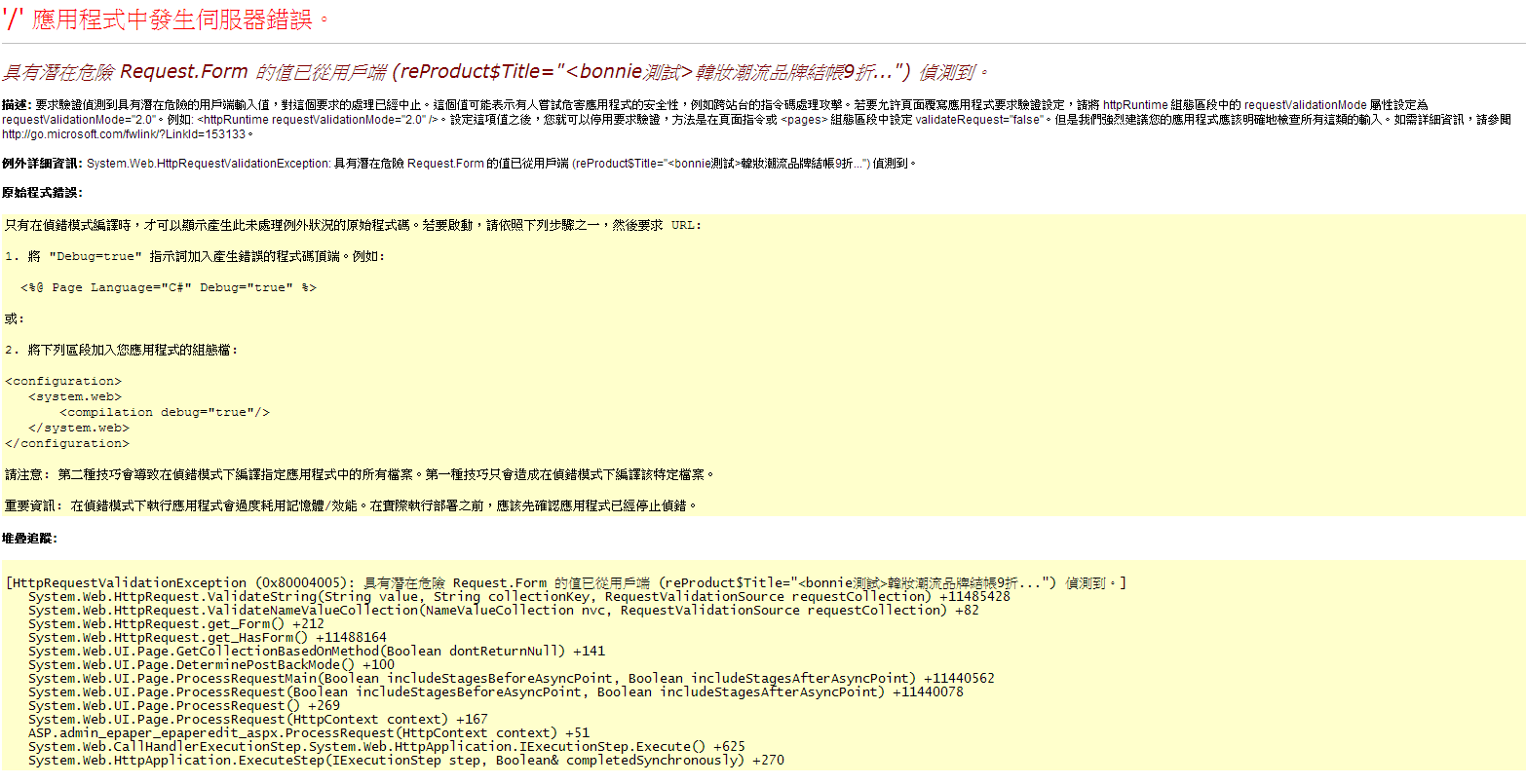
自從網站上了 net4.0 之後,網站會有為數不少的 "潛在危險" 的 exception
大都來自不友善的攻擊,想要測試網站的漏洞
網站做這層防護是好事,只是這個東西太敏感了,連簡單的冒號 & 符號都會跳 exception
更慘的是 Google Analytics 會在一些 user cookies 寫入xml文字 ( __utmz=... )
導致正常的 User 都不能正常瀏覽我們網站
解法有兩種:
1. 直接在 web.config 直接設定 不檢查
2. 自訂 RequestValidate (4.0以上才可以用)
請參考此文章 http://msdn.microsoft.com/en-us/library/system.web.util.requestvalidator(v=vs.100).aspx
大都來自不友善的攻擊,想要測試網站的漏洞
網站做這層防護是好事,只是這個東西太敏感了,連簡單的冒號 & 符號都會跳 exception
更慘的是 Google Analytics 會在一些 user cookies 寫入xml文字 ( __utmz=... )
導致正常的 User 都不能正常瀏覽我們網站
解法有兩種:
1. 直接在 web.config 直接設定 不檢查
<system.web>
<httpRuntime requestValidationMode="2.0" />
<pages validateRequest="false" />
</system.web>
2. 自訂 RequestValidate (4.0以上才可以用)
請參考此文章 http://msdn.microsoft.com/en-us/library/system.web.util.requestvalidator(v=vs.100).aspx
後者比較算是正解 基本上處理掉 <script 我想 XSS 就解決一大半
darren, 2014/7/22 上午 11:53:17
今天設計反應新增電子報時發生問題
解決方式
1. 先確認 aspx => ValidateRequest="false
2. 上面如果設定對

解決方式
1. 先確認 aspx => ValidateRequest="false
2. 上面如果設定對
在Web.config中<system.web>中加入
這段 <httpRuntime requestValidationMode="2.0" />就ok了!!!
造成的原因
是.NET 4.0跟2.0版本在請求驗證的定義不同:
ASP.NET Request Validation 請求驗證是ASP.NET提供來保護XSS攻擊的一項功能
在2.0 僅針對.aspx及class進行驗證…
但到了4.0,請求驗認範圍擴大到所有的請求…
而不是只有.aspx,還包含WebService呼叫以及自訂的http Handlers,都會去驗證http請求的內容…
Vicky, 2014/5/19 上午 11:24:52
假如你現在在ASP.NET 4.0 的環境下的話,就算進行上述的設定,可能仍會出現驗證失敗的訊息(潛在危險Request.QueryString的錯誤訊息)
因為ASP.NET4.0與2.0版本在請求驗證的定義上已經有所不同:
這時為了避免這樣的問題,一樣在Web.Config中 <system.web>下加入下列語句
<httpRuntime requestValidationMode="2.0" />
http://www.dotblogs.com.tw/pin0513/archive/2010/10/22/18522.aspx
因為ASP.NET4.0與2.0版本在請求驗證的定義上已經有所不同:
這時為了避免這樣的問題,一樣在Web.Config中 <system.web>下加入下列語句
<httpRuntime requestValidationMode="2.0" />
http://www.dotblogs.com.tw/pin0513/archive/2010/10/22/18522.aspx
Doug, 2014/3/28 下午 05:35:11
常用的 rule 可以參考:
http://docs.jquery.com/Plugins/Validation/Methods#List_of_built-in_Validation_methods
之中 Methods 的章節,要注意的是 minlength, maxlength, rangelength 三個參數的 length 是小寫,有一些 Blog 會把 L 寫成大寫,然後試半天都試不出來 :P
限定 5 ~ 20 個英文字元或數字的寫法:
passwordformat: true
http://docs.jquery.com/Plugins/Validation/Methods#List_of_built-in_Validation_methods
之中 Methods 的章節,要注意的是 minlength, maxlength, rangelength 三個參數的 length 是小寫,有一些 Blog 會把 L 寫成大寫,然後試半天都試不出來 :P
限定 5 ~ 20 個英文字元或數字的寫法:
passwordformat: true
jQuery.validator.addMethod("passwordformat", function(value, element) {
return value.match(new RegExp("^[a-zA-Z0-9]{5,20}$"));
});
Bike, 2012/10/17 下午 06:51:29
A potentially dangerous Request.Form value was detected from the client (ContentBody_txtContent="<style type="text/cs...").
.aspx新增了<%@ Page validateRequest="false"%>
最後找到還需要在web.config裡面新增<httpRuntime requestValidationMode="2.0" />
相關專案: SINGTEX
Reiko, 2012/4/13 下午 07:32:35