頁數 1 / 2
下一頁
搜尋 validation 結果:
我們會使用 Validation Attribute 來客製化 Validation 的輸出結果,但在 .Net 7 的專案突然失效了。原因是 [ApiController] 會自動回傳 400 錯誤,攔截了 Validation Attribution 的執行。
解決方法, 在 program.cs 中加上以下的程式碼:
builder.Services.Configure<ApiBehaviorOptions>(options
=> options.SuppressModelStateInvalidFilter = true);
解決方法, 在 program.cs 中加上以下的程式碼:
builder.Services.Configure<ApiBehaviorOptions>(options
=> options.SuppressModelStateInvalidFilter = true);
Bike, 2023/3/2 下午 03:27:53
對 DateTime 的 property 直接設定 Require 的 Validation 會失敗. 因為茌是 client 送來空白, 會發生轉型的錯誤, 而不是 Require 的錯誤
可以把該 property 改設定為 DateTime? 來解決這個問題.
可以把該 property 改設定為 DateTime? 來解決這個問題.
Bike, 2021/9/23 下午 10:26:41
錯誤訊息:
WebForms UnobtrusiveValidationMode 需要 'jquery' 的 ScriptResourceMapping。請加入 ScriptResourceMapping 命名的 jquery (區分大小寫)。
解決方式:
在有用 validation 那頁的 Page_Load 加上,就恢復正常了
protected void Page_Load(object sender, EventArgs e)
{
UnobtrusiveValidationMode = UnobtrusiveValidationMode.None;
}
參考來源:
https://blog.xuite.net/tolarku/blog/63451508-VS+2012+%E5%88%9D%E9%AB%94%E9%A9%97+-+%E9%9C%80%E8%A6%81+%27jquery%27+%E7%9A%84+ScriptResourceMapping+%E9%8C%AF%E8%AA%A4
https://www.c-sharpcorner.com/UploadFile/cd7c2e/enabling-unobtrusive-validation-mode-in-Asp-Net-4-5/
WebForms UnobtrusiveValidationMode 需要 'jquery' 的 ScriptResourceMapping。請加入 ScriptResourceMapping 命名的 jquery (區分大小寫)。
解決方式:
在有用 validation 那頁的 Page_Load 加上,就恢復正常了
protected void Page_Load(object sender, EventArgs e)
{
UnobtrusiveValidationMode = UnobtrusiveValidationMode.None;
}
參考來源:
https://blog.xuite.net/tolarku/blog/63451508-VS+2012+%E5%88%9D%E9%AB%94%E9%A9%97+-+%E9%9C%80%E8%A6%81+%27jquery%27+%E7%9A%84+ScriptResourceMapping+%E9%8C%AF%E8%AA%A4
https://www.c-sharpcorner.com/UploadFile/cd7c2e/enabling-unobtrusive-validation-mode-in-Asp-Net-4-5/
choco, 2019/7/9 上午 09:37:20
突然發現 yahoo 不支援 SSL3.0 或 TLS 1.0 了, 要改用 TLS 1.2 才抓的到網頁資料
.Net 4.0 在抓網頁之前先加這兩行, 就可以了.
.Net 4.5 支援 Tls12, 可以用
ServicePointManager.ServerCertificateValidationCallback = delegate { return true; };
ServicePointManager.SecurityProtocol = (SecurityProtocolType)3072;.Net 4.0 在抓網頁之前先加這兩行, 就可以了.
.Net 4.5 支援 Tls12, 可以用
ServicePointManager.ServerCertificateValidationCallback = delegate { return true; };
ServicePointManager.SecurityProtocol = SecurityProtocolType.Tls12;Bike, 2017/7/31 下午 09:35:43
Post 的資料好像會變大, 要改 Web.config
程式碼如下:
<system.web>
<httpRuntime requestValidationMode="2.0" maxRequestLength="1024000"/>
</system.web>
程式碼如下:
public string UploadFilesToRemoteUrl(string url, string[] files, NameValueCollection formFields = null)
{
string boundary = "----------------------------" + DateTime.Now.Ticks.ToString("x");
HttpWebRequest request = (HttpWebRequest)WebRequest.Create(url);
request.ContentType = "multipart/form-data; boundary=" +
boundary;
request.Method = "POST";
request.KeepAlive = true;
Stream memStream = new System.IO.MemoryStream();
var boundarybytes = System.Text.Encoding.ASCII.GetBytes("\r\n--" +
boundary + "\r\n");
var endBoundaryBytes = System.Text.Encoding.ASCII.GetBytes("\r\n--" +
boundary + "--");
string formdataTemplate = "\r\n--" + boundary +
"\r\nContent-Disposition: form-data; name=\"{0}\";\r\n\r\n{1}";
if (formFields != null)
{
foreach (string key in formFields.Keys)
{
string formitem = string.Format(formdataTemplate, key, formFields[key]);
byte[] formitembytes = System.Text.Encoding.UTF8.GetBytes(formitem);
memStream.Write(formitembytes, 0, formitembytes.Length);
}
}
string headerTemplate =
"Content-Disposition: form-data; name=\"{0}\"; filename=\"{1}\"\r\n" +
"Content-Type: application/octet-stream\r\n\r\n";
for (int i = 0; i < files.Length; i++)
{
memStream.Write(boundarybytes, 0, boundarybytes.Length);
var header = string.Format(headerTemplate, "uplTheFile", files[i]);
var headerbytes = System.Text.Encoding.UTF8.GetBytes(header);
memStream.Write(headerbytes, 0, headerbytes.Length);
using (var fileStream = new FileStream(files[i], FileMode.Open, FileAccess.Read))
{
var buffer = new byte[1024];
var bytesRead = 0;
while ((bytesRead = fileStream.Read(buffer, 0, buffer.Length)) != 0)
{
Response.Write("bytesRead: " + bytesRead.ToString() + "<br>");
memStream.Write(buffer, 0, bytesRead);
}
}
}
memStream.Write(endBoundaryBytes, 0, endBoundaryBytes.Length);
request.ContentLength = memStream.Length;
using (Stream requestStream = request.GetRequestStream())
{
memStream.Position = 0;
byte[] tempBuffer = new byte[memStream.Length];
memStream.Read(tempBuffer, 0, tempBuffer.Length);
memStream.Close();
requestStream.Write(tempBuffer, 0, tempBuffer.Length);
}
try
{
using (var response = request.GetResponse())
{
Stream stream2 = response.GetResponseStream();
StreamReader reader2 = new StreamReader(stream2);
return reader2.ReadToEnd();
}
}
catch (Exception ex)
{
return (ex.ToString());
throw;
}
}
Bike, 2017/1/12 下午 08:21:09
自從網站上了 net4.0 之後,網站會有為數不少的 "潛在危險" 的 exception
大都來自不友善的攻擊,想要測試網站的漏洞
網站做這層防護是好事,只是這個東西太敏感了,連簡單的冒號 & 符號都會跳 exception
更慘的是 Google Analytics 會在一些 user cookies 寫入xml文字 ( __utmz=... )
導致正常的 User 都不能正常瀏覽我們網站
解法有兩種:
1. 直接在 web.config 直接設定 不檢查
2. 自訂 RequestValidate (4.0以上才可以用)
請參考此文章 http://msdn.microsoft.com/en-us/library/system.web.util.requestvalidator(v=vs.100).aspx
大都來自不友善的攻擊,想要測試網站的漏洞
網站做這層防護是好事,只是這個東西太敏感了,連簡單的冒號 & 符號都會跳 exception
更慘的是 Google Analytics 會在一些 user cookies 寫入xml文字 ( __utmz=... )
導致正常的 User 都不能正常瀏覽我們網站
解法有兩種:
1. 直接在 web.config 直接設定 不檢查
<system.web>
<httpRuntime requestValidationMode="2.0" />
<pages validateRequest="false" />
</system.web>
2. 自訂 RequestValidate (4.0以上才可以用)
請參考此文章 http://msdn.microsoft.com/en-us/library/system.web.util.requestvalidator(v=vs.100).aspx
後者比較算是正解 基本上處理掉 <script 我想 XSS 就解決一大半
darren, 2014/7/22 上午 11:53:17
今天設計反應新增電子報時發生問題
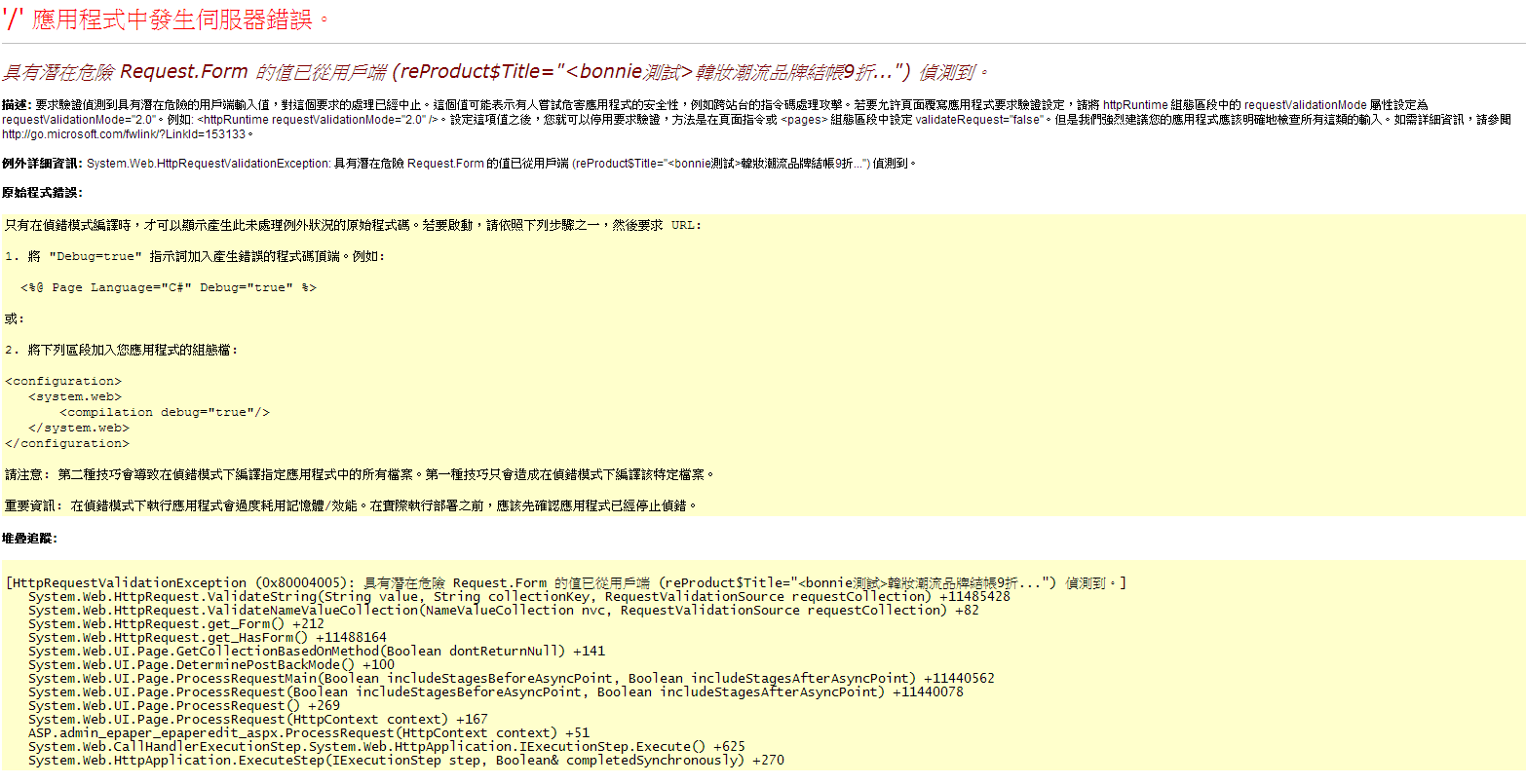
解決方式
1. 先確認 aspx => ValidateRequest="false
2. 上面如果設定對

解決方式
1. 先確認 aspx => ValidateRequest="false
2. 上面如果設定對
在Web.config中<system.web>中加入
這段 <httpRuntime requestValidationMode="2.0" />就ok了!!!
造成的原因
是.NET 4.0跟2.0版本在請求驗證的定義不同:
ASP.NET Request Validation 請求驗證是ASP.NET提供來保護XSS攻擊的一項功能
在2.0 僅針對.aspx及class進行驗證…
但到了4.0,請求驗認範圍擴大到所有的請求…
而不是只有.aspx,還包含WebService呼叫以及自訂的http Handlers,都會去驗證http請求的內容…
Vicky, 2014/5/19 上午 11:24:52
假如你現在在ASP.NET 4.0 的環境下的話,就算進行上述的設定,可能仍會出現驗證失敗的訊息(潛在危險Request.QueryString的錯誤訊息)
因為ASP.NET4.0與2.0版本在請求驗證的定義上已經有所不同:
這時為了避免這樣的問題,一樣在Web.Config中 <system.web>下加入下列語句
<httpRuntime requestValidationMode="2.0" />
http://www.dotblogs.com.tw/pin0513/archive/2010/10/22/18522.aspx
因為ASP.NET4.0與2.0版本在請求驗證的定義上已經有所不同:
這時為了避免這樣的問題,一樣在Web.Config中 <system.web>下加入下列語句
<httpRuntime requestValidationMode="2.0" />
http://www.dotblogs.com.tw/pin0513/archive/2010/10/22/18522.aspx
Doug, 2014/3/28 下午 05:35:11
常用的 rule 可以參考:
http://docs.jquery.com/Plugins/Validation/Methods#List_of_built-in_Validation_methods
之中 Methods 的章節,要注意的是 minlength, maxlength, rangelength 三個參數的 length 是小寫,有一些 Blog 會把 L 寫成大寫,然後試半天都試不出來 :P
限定 5 ~ 20 個英文字元或數字的寫法:
passwordformat: true
http://docs.jquery.com/Plugins/Validation/Methods#List_of_built-in_Validation_methods
之中 Methods 的章節,要注意的是 minlength, maxlength, rangelength 三個參數的 length 是小寫,有一些 Blog 會把 L 寫成大寫,然後試半天都試不出來 :P
限定 5 ~ 20 個英文字元或數字的寫法:
passwordformat: true
jQuery.validator.addMethod("passwordformat", function(value, element) {
return value.match(new RegExp("^[a-zA-Z0-9]{5,20}$"));
});
Bike, 2012/10/17 下午 06:51:29

※修改主目錄web.config
刪除(紅字)
*<compilation debug="true" targetFramework="4.0">
*<httpRuntime maxRequestLength="102400" requestValidationMode="2.0"></httpRuntime>

※修改虛擬目錄web.config
加上<remove assembly="...." />

1.如果网站程序不需要ASP.NET 4.0 的支持,那么可以直接配置网站使用ASP.NET 2.0。
2.如果网站程序需要ASP.NET 4.0的支持,就需要将该网站下使用ASP.NET 2.0的虚拟目录移动到其他网站。
3.如果上面两种方法都不适用于你的实际情况,那么就只能用这种方法了:
打开注册表找到“HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\ASP.NET\\4.0.30319.0”
添加键值名为“EnableExtensionlessUrls” 类型为“DWORD”的键值
并设置值为"0"
然后在cmd中运行“IISRESET”,重启IIS以读取注册表修改后的内容。
(重啟該應用程式集區即可):
注:此项修改就是关闭ASP.NET 4.0对无扩展URL的处理,若将此项键值设为“1”则开启。
參考:http://www.webjx.com/aspnet/2011-04-02/29024.html
Reiko, 2012/4/16 下午 01:23:51